Google Cloud Incidents
The built-in Google Cloud Incidents trigger initiates a flow when it receives a signal from a Google Cloud's operations suite webhook.
Add the Google Cloud Incidents trigger to the canvas
- Go to the Triggers tab in the palette, expand the App Triggers section and drag the trigger onto the canvas.
- Double-click the trigger (or click the pencil icon).
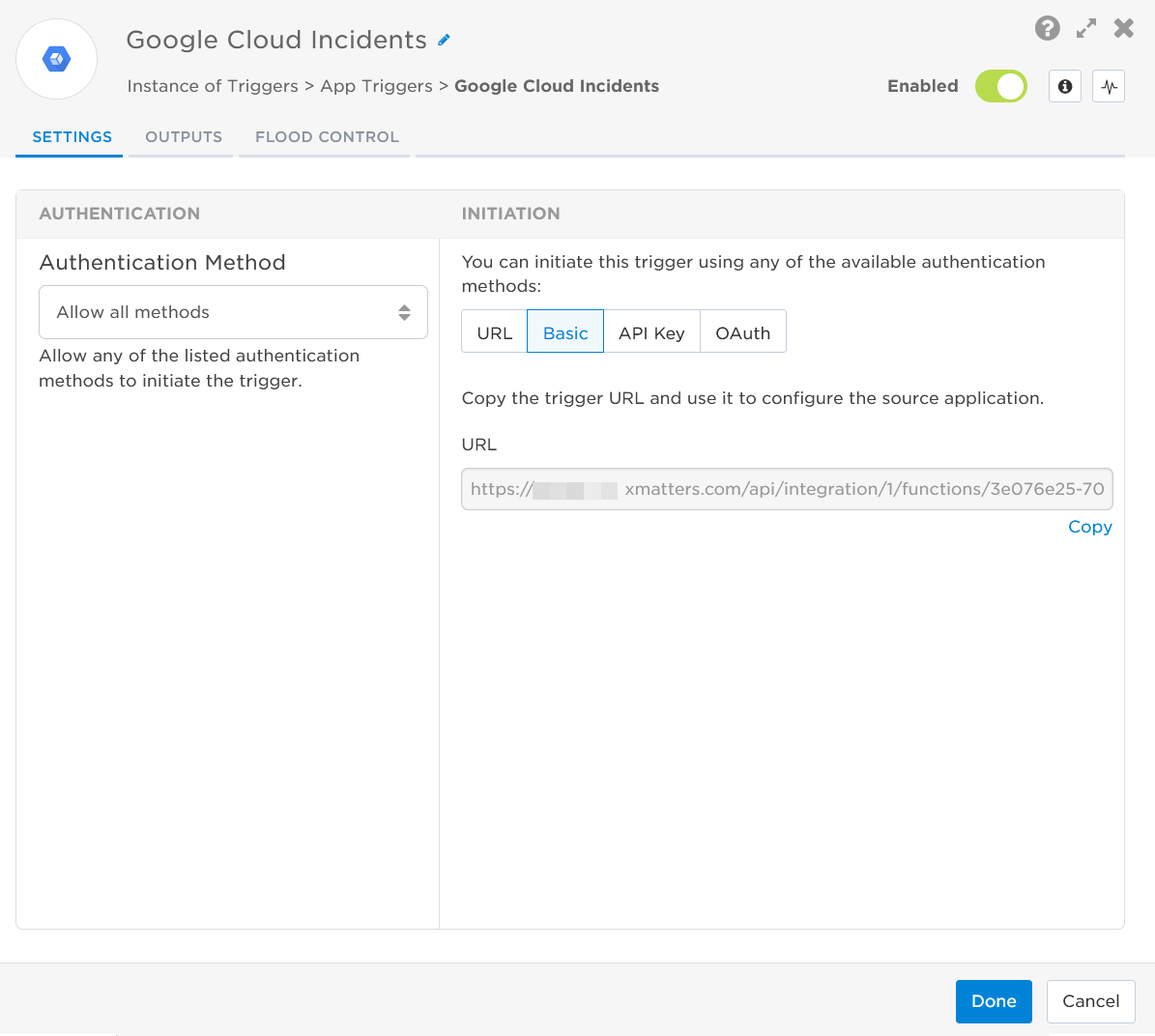
- Select the authentication method: URL or Basic.
- If using URL authentication, select the authenticating user, and then copy the URL — you'll use this to set up the webhook in Google.
- If using Basic authentication, all you need is the credentials for the authenticating xMatters user.
- Click the Flood Control tab to edit the trigger's default flood control settings. For more information about these settings, see Trigger Flood Control.
- Click Done.
- On the flow canvas, connect the steps you want to run when xMatters receives a request to that URL.
You're now ready to configure Google Cloud to target the trigger.
Configure Google Cloud to send requests to the trigger URL
To have Google send alerts to the flow trigger, you need to enter the trigger URL when you create a notification webhook.
- In Google Cloud's operations suite, go to Monitoring > Alerting.
- Click Edit Notification Channels.
- In the Webhooks section, click Add New.
- Paste the URL you copied from xMatters in the Endpoint URL field and give your webhook a name.
- If you want to use basic authentication, select the check box and enter the web login and password of an xMatters user.
- Add the target names of any recipients you want xMatters to notify when the alert fires.
- For URL authentication, use an ampersand to attach recipients. For example, if you want to notify Emma Pearson and the on-call members in the group responsible for the Antares service, you'd add &recipients=epearson,antares to the end of the URL.
- For other authentication types, use a question mark to attach recipients. For example, if you want to notify Barry Gull and the on-call members in the group responsible for the Cassiopeia service, you'd add ?recipients=bgull,cassiopeia to the end of the URL.
- You must URL-encode any special characters or spaces in the target names.
- Click Test Connection to send a test message to xMatters.
- This won't cause any notifications to be sent, but you can check the Activity Stream to see if the message came through.
- After you test the connection, click Save.
- Open the alerting policy that you want to send alerts to xMatters (or create a new one).
- Click Add Notification Channel.
- In Who should be notified?, select the webhook you created as the notification channel.
- Make sure to select the Notify on incident resolution check box if you want xMatters to automatically terminate events related to the resolved incident.
- Click Add.
You're ready to use the webhook to trigger automated flows, including steps such as sending alerts and initiating incidents, though we always recommend testing before putting things into use.
Outputs
The trigger has the following outputs you can use as inputs to steps further along the flow.
|
Label |
Description |
|---|---|
|
Recipients |
List of targeted recipients. Recipients are set by adding a recipients query parameter to the trigger URL when you configure the webhook in Google. See the instructions for configuring the webhook for details. |
| Signal Mode | Determines the path the flow will take, based on the values of State and Incident ID: if State is open, Signal Mode is set to Alert; if State is closed, Signal Mode is set to Clear; if Incident ID is test, Signal Mode is set Test. |
| Signal ID | Key or identifier used to terminate or correlate signals. The Signal ID is set to Incident ID. |
| Condition Name | Descriptive name of the condition that fired. |
| Incident ID | Unique identifier of the instance of the incident in Google Cloud Monitoring. This sets the Signal ID. If the Incident ID is test, it's also used to set the Signal Mode to Test. |
| Metric Display Name | Metric related to the alert condition. |
| Policy Name | Name of the alert policy that triggered the incident. |
| Resource Name | Name of the resource that was checked. |
| Started At | Time the incident was created in Google Cloud. |
| State | Current state of the incident (open or closed). This value is used to determine the Signal Mode value. |
| Summary | Brief description of the incident in Google Cloud. |
| URL | Direct link to the incident in Google Cloud Monitoring. |
| Raw Request | JSON representation of the request. You can parse the raw request if you need additional details beyond the standard outputs. |